PKI: Public Key Infrastructure
PKI is a set of roles, policies and procedures needed to create, manage, distribute, use, store, and revoke digital certificates, and manage public-key encryption. Here the binding of the public key to respective identities, like people or organisation is done. In public environment, where third-party verifications are required, this PKI is used. There are three parties involved here-
-
Registration authority
-
Validation Authority
-
Certification authority
When a user needs a public key certificate he first goes to the certification authority, which then redirects him to the registration authority. RA collects all information like name, personal identity information, public key, etc., and creates a certificate and passes it on to the certification authority. The certifying authority gets one copy of the certificate and signs it using the private key, authorising the public key of the user. One copy is stored in the database of validation authority; at any future point in time, the user’s public key can be verified with validation authority.
Every certificate issued by CA has an expiry date, the private key of CA and the public key of the user. Upon expiry, or if stolen, the certificate can be renewed or re-issued.
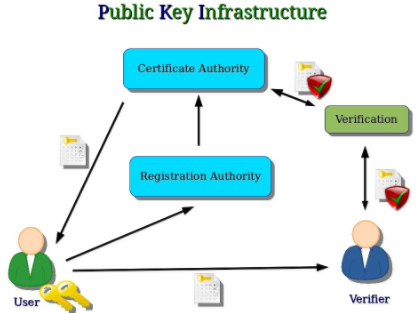
Image Source: https://computersecuritypgp.blogspot.in/2016/05/public-key-infrastructure-and-blockchain.html