Introduction to Cryptography
Cryptography is the art of converting text into another form for secret transmission and reception. It works by converting plain text into cipher text using some encryption algorithm at the sender’s side and converting ciphertext into plain text at the receiver’s. Cryptography is used to provide confidentiality, integrity, authenticity and non-repudiation.
Key terms:
Plain text: Message to be encrypted
Ciphertext: Encrypted message
Encryption: Process of converting plain text into cipher text.
Decryption: Process of converting ciphertext into plain text.
Algorithm: The method used to encrypt/decrypt the plain text.
Key: The data used for encrypting/decrypting.
There are various cryptographic algorithms present, generally we categorise them as follows-
Symmetric cryptography:
Here one single key is used for encryption and same key is used for decryption. DES and AES are examples of symmetric key cryptography.
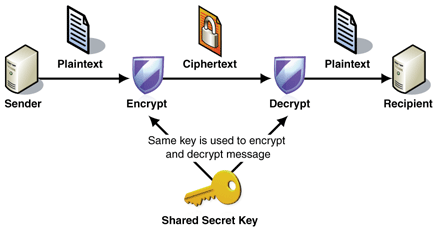
Image Source: http://www.jayitsecurity.com
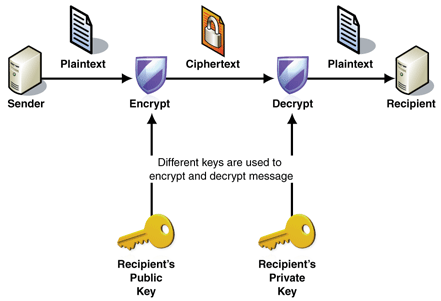
Asymmetric cryptography/Public key cryptography:
Here two keys are used, Public key is used for encryption and Private key is used for decryption; e.g. RSA.
Block Cipher:
The input plain text is broken into fixed size blocks and they are encrypted /decrypted as a block; e.g. DES, AES.
Stream cipher:
The incoming data is encrypted or decrypted byte by byte; e.g. RC4.
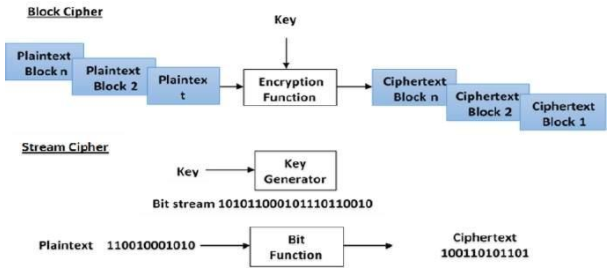
Image Source: https://www.tutorialspoint.com/cryptography/modern_symmetric_key_encryption.htm
Digital Signatures:
Digital signatures are used to identify the genuinity of the source; the sender signs with his private key, and at the receiver’s end it can be decrypted only with the public key of the sender. This enables the receiver to know who has sent the message.
Hash Algorithms:
Hash algorithms are used to maintain the integrity of the data by finding a definite number for the file and verifying it at the receiver’s end.
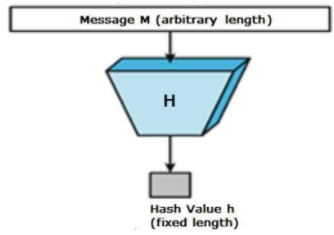
Image Source: https://www.tutorialspoint.com/cryptography/cryptography_hash_functions.htm
At the sender’s side, the hash algorithm generates a fixed size number for any-sized file. This number or hash value is sent along with the cipher text to the receiver. At the receiver’s end, the cipher text is first decrypted, and then using hash algorithm a hash value is generated. If the hash value matches with the hash value that came with the cipher text, then the message was not corrupted. If it is different, then we can understand that the message has been intercepted and modified.
There are various hash algorithms
SHA1, SHA 256 , MD5, etc.