Injection Flaws
SQL Injection:
User login screens, URLs, search boxes are the point of interest to an attacker since they are dynamic inputs, based on which web application requests are constructed. If an attacker is successful in making the browser construct a malicious query and get it executed by the back-end database, it is called SQL injection. An attacker may modify, delete or even do a DOS attack on the database.
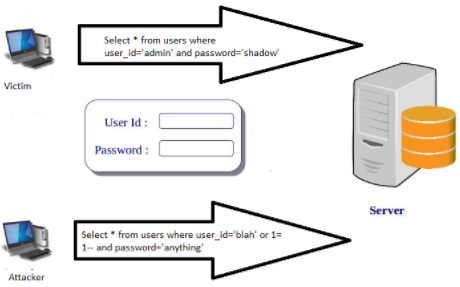
Source: http://computersecuritypgp.blogspot.com/2016/01/what-is-sql-injection-attack.html
Command Injection:
If a user is able to inject operating system commands on any user input field, it may lead to attacker injecting malicious commands to get sensitive information from the web server.
LDAP injection:
Lightweight Directory Access Protocol is an active directory on IP, where the information is arranged in a hierarchical manner based on user attributes. LDAP injection works the same as SQL injection where the attacker tries to enter arbitrary data to craft malicious queries to be executed by the LDAP server.
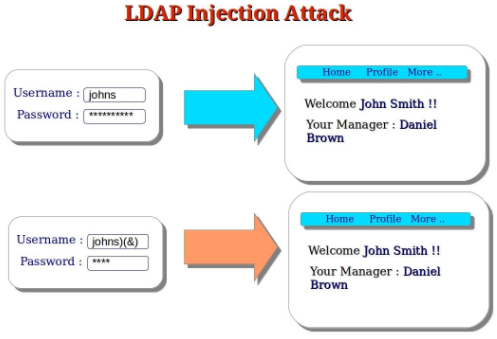
Source: http://computersecuritypgp.blogspot.com/2016/01/what-is-ldap-injection-attack.html