Top 10 Must-Have tools to perform Steganography
Introduction
In this article, we will be discussing what steganography is, how it is different from cryptography and what are the available tools that can be used to do this. Do we really need this in the first place? The roots of steganography go long back to 440 BC. Let’s discuss a couple of examples from the past:
Chinese Technique: Text written on silk and then made it into a ball covered with wax. The ball was then swallowed by the messenger.
Second World War: Shrinking a whole text page into a tiny dot (1 mm approx) and then that dot can be used in the usual text (maybe the first dot in the common text).
Messages are written in morse code on a knitting yarn which is used to make the cloth for the package.
The techniques have evolved much since then from physical steganography to technology-oriented steganography.
So, without wasting much time let’s get started!
What is Steganography?
Steganography has evolved from the Greek word “Steganos” meaning hidden or covered. Steganography is the art of hiding a secret message into an ordinary object. The secret message and ordinary objects can be an image, text, audio, files etc. A user can hide the secret in an ordinary looking object using some tools and techniques and the receiver can then use the similar technique to get the secret back.
Steganography is required to send the message without disclosing the presence of the message. This is how steganography differs from cryptography. Cryptography ensured that the message is encrypted and this crypto message will not make any sense to the user without decryption. A malicious user can intercept this message and try to recover the message or the key used to encrypt the message using cryptographic attacks (Here's a resource that will navigate you through cyber security attacks). Steganography ensures that the object in which the message is hidden will not attract the hackers to try and get the message as there is no sign that there is something in the ordinary looking object. For example, a sender might send an ordinary looking pdf file which might have a toolkit installed in it. One such example is of stegosploit, Stegosploit is a tool used to analyze images that may contain hidden messages. To get that toolkit the user has to read the PDF present in the link here.
The point of interest here is that the toolkit is hidden in the PDF and the user needs to read the article completely in order to retrieve the toolkit using steganographic techniques. I will leave this to the reader’s interest if they want to give it a shot to capture the kit.
In a nutshell, steganography is hiding the message whereas cryptography is converting the message into non-human readable form. Steganography provides security through obscurity. If no one can see it no one can crack it.
You may also like: How much can a Certified Ethical Hacker earn in 2018?
Types and forms of Steganography
Steganography can be broadly classified into two types’ Technical and Digital. Technical steganography will deal with the methods that involve physical means to hide the text like writing it on the clay tablet with invisible ink or use of microdots discussed previously. These methods are effective but old school.
With the digital age in full power, steganography has become digital too. It uses various techniques like altering the image pixels to hide the message, injecting the text into a cover message, hiding the messages in the white spaces of the files etc. This is achieved with the use of various transform functions and concealment algorithms. Today most of the tools do not perform steganography alone. It is combined with cryptography to add an extra layer of security. Now even if the image is analyzed for steganography the analyzer has to break the crypto in order to get the message. This also poses a question that is the hidden message worth all this work?
Steganography can have various forms depending on the type of message, cover message and the tool used. The message and cover can be text, images, audio, video, HTML pages etc. Different tools provide various forms but the most widely used is hiding image or text in another image. Since images are harmless and do not pose any threat.
Top 10 tools to perform Steganography
1. Xiao Steganography
Xiao Steganography is developed by Nakasoft and can be used to perform steganography for bump and wav files. The tools are available for windows platform and are extremely simple to use with 3 easy steps that will be discussed below.
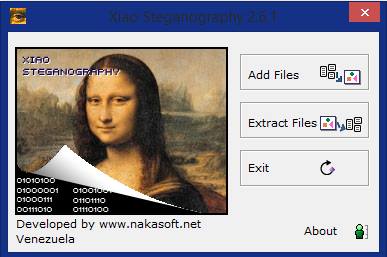
Image Source: http://bit.ly/2xWBU11
Step 1: Select the target file (Image and wav file only supported).
Step 2: Select the file that has to be added to the target file (can be any file: choose a text file for testing).
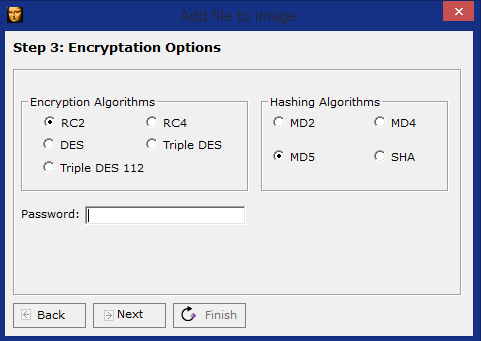
The tool offers RC2, RC$, DES, Triple DES, Triple DES 12 encryption along with a few hashing options. Triple DES can be used to provide a stronger encryption along with MD5 hash. The file can be password protected and all these combined provides a strong steganography as well as crypto options.
Step 3: Choose encryption, hashing, and password for target file and click finish. You are asked to save the file and done (also consider checking out this career guide for cyber security Jobs).
The tool can be downloaded here.
2. Steghide
Steghide is one of the cross-platform steganography software that has been developed by Stefan Hetzl. The tool can be used to hide various kind of data in images and audio files. The tool can hide data in JPEG, BMP, Wav and AU files. The data that is embedded is compressed, encoded and tagged with integrity checksums. The users can choose the encryption algorithm but the default encryption used is Rijndael in CBC mode with the 128-bit key, along with the CRC32 checksum.
You may also like: Brute Force Attacks: Prominent Tools to Tackle Such Attacks
Here is how the tool works:
First: Secret data is compressed and encrypted.
Second: Using a passphrase, a series of pseudo-random numbers is generated and the pixels of the covert at those locations are used to hide the data.
Third: The tool uses the graph theory matching algorithm to generate a pair of pixels and that are exchanged to hide the data. (Mathematical stuff inside). The tool can be downloaded here.
The tool is licensed under GPL and the source code is also available at the link for modification and public release.
3. S-Tools
S-Tools is an extremely simple tool that can be used to hide text files in images. The toolkit can be downloaded here.
The tool is present in zip format, just extract it and create a simple text file which has the data you want to hide. Save a cover photo in which the data will be hidden. Just run the .exe file and drag the BMP file to that window. Then drag the text file over the image and select the encryption algorithm to embed the file. The options available are IDEA, DES, triple DES etc. Select a passphrase that will be used to reveal the hidden files from the images. Just use the same process to reveal the contents that have been hidden in the file.
4. Invisible Secrets 4
This is enterprise software from East-tec Corporation and can be used to encrypt and hide files that are critical to the organization. The files can be hidden in any of these carriers: JPEG, PNG, BMP, HTML, Wav files. This software has a lot of other capabilities like email encryption, password manager, file shredder, application locker, IP-IP password transfer, crypto-board etc. The tool is paid but a trial version can be downloaded from the link given here.
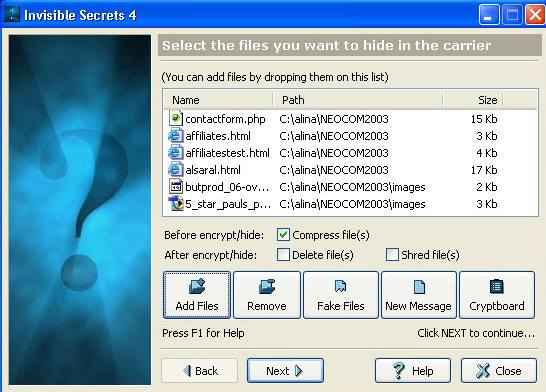
Image Source: https://www.east-tec.com
5. Snow
Snow is a fast tool that takes that advantage of the fact that spaces and tabs at the end of the lines are invisible when displayed in text editors. Snow uses these white spaces to hide the text. Since space is less hence it will be difficult to embed a large file thus there is a serious need for compression. Here is the step by step working of the tool while some of the steps may be optional:
Secret message > Compression > encryption> secret concealed in text → Extract data from text > Decode > Uncompressing > Secret message
You may also like: Top 15 Prominent Wireless Hacking Tools to watch out for in 2018
Snow uses Huffman encoding as the compression technique and provides a 25-40% of compression. In case the message is large it is better to compress it separately and then conceal it in the carrier message. Encoding technique used by snow is ICE with 64-bit block cipher running in cipher feedback mode. The tool can be downloaded here along with an extremely elaborative literature on the tool.
6. Hide ‘N’ Send
This is a small and extremely simple tool that can be used to hide files in image files. Just run the utility and select the files, select the encryption, concealment and hashing algorithms and click hide. The tool has just two tabs for hiding and extraction. The tool can be downloaded here.
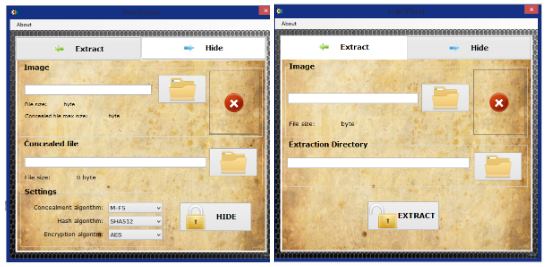
7. Blindside
A blindside is a free tool that is freely available for usage and distribution. Blindside can be used to hide any kind of data in BMP images. Like other software this software also uses both steganography as well as cryptography techniques for hiding the images. A lot of other softwares which have similar functionality are present but this one has some edge over others. Other softwares stores the data in the LSB (Least significant bit) of every pixel. This may cause a distortion or a noticeable change in the image thus defeating the purpose of steganography. There are over 16 billion colors and the human eye cannot differentiate between then accurately. Blindside takes advantage of this fact and alters only those pixels that will not be noticeable to the human eye by analyzing the pixels. This has one negative side as well. The overall space to embed the data gets reduced due to this pixel color analysis. The tool has a special feature to check how much data can be stored in the image. Each image can be analyzed for data hiding space just like a removable pen drive, great right? Blindside is a cross-platform command line based tool and can perform a couple of functions:
Encrypt and hide files in an image:
B SIDE -a (source image) (file to be hidden) (output file name) (password)
Decrypt and restore the hidden files:
B SIDE -x (file with hidden contents) (file to be retrieved) (password)
List of hidden contents (along with file sizes):
B SIDE -L (file with hidden contents)
Check for space availability:
B SIDE -c (file in which data has to be embedded)
You may also like: Top 20 Trending Computer Forensics Tools of 2018
8. Image-Steganography
Whether you're using your own images or even those generated by an AI image generator, this tool provides an easy and convenient way to embed one image within another without the need to download additional software. Just select the files and select the hidden bits. It runs on the concept of replacing the Least Significant Bit of the pixel with the most significant bits of the message.
Example: (convert the numbers into 8-bit values and try)
Envelope pixel (red, green, blue): 167, 93, 27
Secret pixel (red, green, blue): 67, 200, 105
Output pixel (red, green, blue): 162, 94, 27
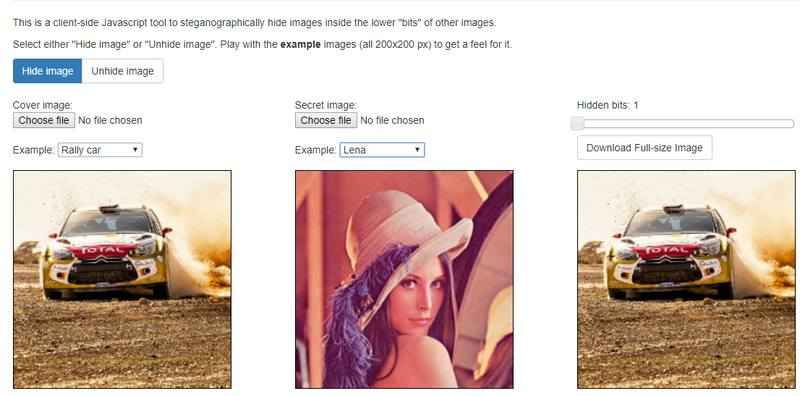
(Bit setting 1: One least significant bit is changed with one most significant bit): Least distortion
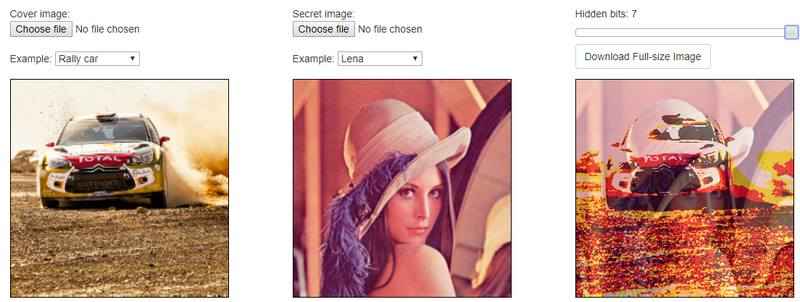
(With bit set to 7 i.e. 7 bits are changed out of 8): Most distortion
9. Camouflage
Camouflage is a free tool that can be used to hide one file into another. This one is just for windows and the usage is extremely simple. Just right-click a file and select camouflage and do the same for retrieving the files back. The tool is simple to use but the project has been abandoned for some reasons but the software is still available for free usage and distribution. You can hide the file and send it anywhere without getting detected. If you are uploading a file to an FTP server just ensure that you upload a binary file else the file may get corrupted. The tool can be downloaded here.
You may also like: What is a Sniffing attack and How can you defend it?
10. Steganography (Hide text into an image)
This simple online tool can help hide text into images quickly. The tool comes handy if you just want to send a message without any trace of steganography activity. There are a few constraints to this but this is just for small messages and quick usage. The tool link is given here.
Takeaway
With all these tools and knowledge you can be a data hiding ninja now. There is one point that is both positive and negative. The pros are that the data cannot be detected and hence the attacks are less. The concealed message is protected with passwords and crypto algorithms for protection and integrity. On the other side, malicious users can use these techniques for distributing malware, embedding viruses in the images and distributing them. These techniques can be used to transmit information linked to various illegal activities. With the advancements in technology, it is really hard to recover the secret if you are not the intended recipient. More to it, before trying to recover the message it is harder to suspect if the medium might have something hidden inside. Readers are requested not to use these techniques for illegal or criminal purposes.