Top 25 Prominent Wireless Hacking Tools (Updated for 2021)
There was a time when people relied on broadband and mobile data packs for connecting to the internet. With the influx of IoT in our day to day life, the use of WiFi has increased many folds. Every house has almost five to six devices that require the internet to work efficiently. Homes have now become more digitally connected with heavy usage of smart TVs, smart Ac's, smartphones, laptops, smart alarms, etc. Three components related to WiFi have also gone to the next level along with all other advancements:
-
WiFi protocols: We are well aware that the use of WEP has depreciated due to security weaknesses. The protocol stack has developed over time from being highly insecure to the highest level of security possible.
-
Hardware technology: Both the endpoints that use the WiFi and the WiFi router have become advanced. Routers used to come with a single antenna having a small signal range. Now the routers have a bigger range, better signal strength, and multiple antennas pointed in multiple directions so as to kill the blind spots.
-
Wireless attacks: Public WiFi, free WiFi, and personal hotspots on the go have increased the wireless playgrounds that the attackers can target. Attackers can hack into the network and can monitor the traffic in that network or crack the password and use your network for free. Just check the wireless networks that the laptop catches and you can see an example right there!
Before we start digging deep into wireless hacking, let's get a few things straight.
Hacking/attacking unauthorized wireless networks is illegal. The article does not encourage the use of the aforementioned tools for a criminal purpose. These tools are to be used only for educational purposes and to try on your own devices or network. Things are not going to be straightforward; wireless hacking is not as easy as shown in hacking movies. To protect yourself from hacker attacks, we advise everyone to use VPN Google extension or VPN for the Desktop version. VPN hides your IP address and geolocation. VPN tool makes it impossible to hack your device and steal your personal data.
What Is Wireless Hacking?
Due to the increasing usage of wireless networks, wireless attacks are rising at an exponential pace. Wifi networks are commonly vulnerable to hacking as wireless signals can be picked up and exploited anywhere and by anyone.
Wireless hacking can be defined as an attack on wireless networks or access points that offer confidential information such as authentication attacks, wifi passwords, admin portal access, and other similar data. Wireless hacking is performed for gaining unauthorized access to a private wifi network.
The increase in WiFi usage has led to increased wireless attacks. Any attack on wireless networks or access points that provide substantial information is referred to as wireless hacking. This information can be in the form of WiFi passwords, admin portal access, authentication attacks, etc. To understand wireless hacking, one of the most important things to understand are the protocols involved in wireless networks. Attacks are mostly made on the internal steps of the protocol stack. IEEE 802.11 specifies the standards for wireless networks; let us discuss some algorithms that are used in WiFi networks:
-
WEP (Wired Equivalent Privacy): WEP uses a 40-bit key and a 24-bit initialization vector. It uses RC4 for confidentiality and CRC 32 for integrity. Since the initialization vector is of 24 bits, there is a high probability that the same key will be repeated after every 5000 packets. WEP is a depreciated algorithm due to the various vulnerabilities identified and the fact that it can be cracked very easily.
-
WPA and WPA2: WPA was introduced as a temporary solution for the devices that did not support WPA2. WPA has now been broken and depreciated. The WPA2 is considered to be the most secure to date. The tools discussed further in the article will also cover details on how to attack WPA and WPA2 but the success of an attack depends on the time and the computing power.
You may also like: OWASP- Top 10 Vulnerabilities in web applications (updated for 2018)
Attacking Techniques
-
WEP cracking technique: WEP uses a 40-bit key that is 8 characters long. Once enough data packets are captured, breaking this key should not take more than a few minutes.
-
WPA/WPA2 cracking technique: Our devices have wireless passwords stored so that we do not enter the password on the same device again and again. The attackers take advantage of this by forcefully de-authenticating all the devices on the network. The devices will try to auto-connect to the access point by completing the 4-way handshake. This handshake is recorded and has the hashed password. The hashed password can be brute-forced by using a rainbow table.
-
WPS cracking: This technology uses an 8 digit pin to connect to the wireless router. Brute forcing the 8 digit pin will give access to the router. Various tools use various optimization techniques to increase the speed of this attack and crack the key in a couple of hours.
You may also like: Brute Force Attacks: Prominent Tools to Tackle Such Attacks
What Are Wireless Hacking Tools?
Wireless hacking tools are the software programs specifically designed to hack wireless networks by either leveraging dictionary attacks for cracking WEP/WPA protected wireless networks or exploiting susceptibilities in wifi systems.
Hacking or gaining unauthorized access to wireless networks is an illegal act, an activity not encouraged. These wireless hacking tools deploy various techniques to crack wifi networks such as sidejacking, brute force attacks, dictionary attacks, evil twin, encryption, and Man-In-the-Middle Attacks.
We have compiled a list of the best wifi password hacking or recovery tools that can be used for educational purposes and to hack your own systems or wifi networks. If you are looking to become a cybersecurity professional, you would have to understand wifi hacking and learn about wireless technologies.
Here are the top 25 hacking tools and software updated for 2021. They are used for wireless password cracking, network troubleshooting and to analyze wireless systems for potential security issues.
Wireless Hacking Tools Used for Cracking Wireless Password and Network Troubleshooting
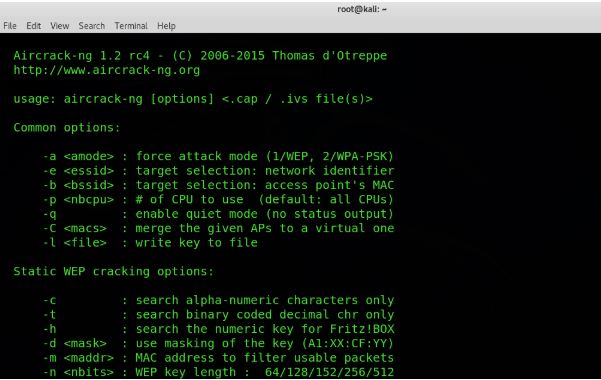
1. Aircrack-ng
Aircrack-ng is one of the most popular suites of tools that can be used to monitor, attack, test, and crack WiFi networks. It is compatible with Windows, Linux, OS X and is a command-line tool. It can be used for attacking and cracking WPA and WEP. The attaching mechanism is simple. It monitors and collects packets, once enough packets are captured; it tries to recover the password.
A few things to ponder upon before you start. You need a wireless card that can inject packets into the network or you won’t be able to crack.
2. AirSnort
AirSnort is free WiFi hacking software that captures the packets and tries to decrypt the keys. The monitoring is done in promiscuous mode and records enough packets to reliably decrypt the key. It is a simple tool and supports both Windows and Linux platforms. Further development and maintenance of this tool has been discontinued but the older version can still be downloaded.
You may also like: SPECTRE and MELTDOWN: How do I know if my PC is at risk?
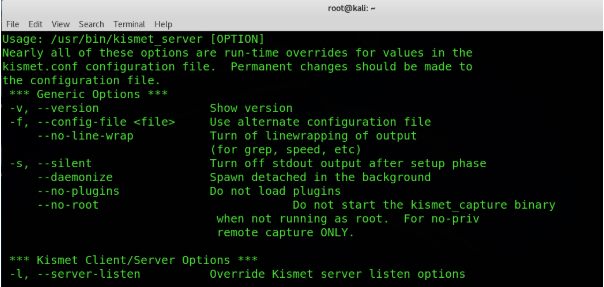
3. Kismet
Kismet is free software written in C++ that can be used to sniff TCP, UDP, DHCP, and ARP packets. It is a passive tool and does not interact with the network. It has the ability to find hidden networks and is used in wardriving kind of activities. The captured packets can be exported to WireShark and can be further analyzed. It is available for Linux, Windows, and a few other platforms.
4. Cain and Abel
Cain & Abel is one of the most popular tools that is used for password cracking. The tool is able to sniff the network, crack encrypted passwords using various password cracking techniques, and perform cryptanalysis attacks. It can also discover wireless keys by analyzing wireless protocols.
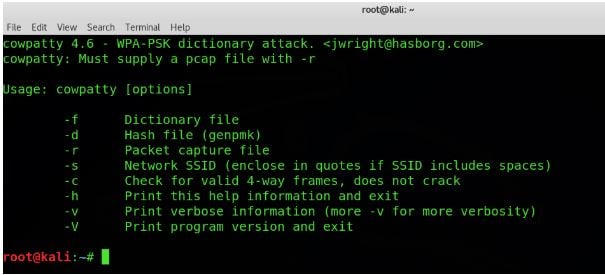
5. CoWPAtty
The name CoWPAtty itself has WPA in uppercase and rest in small letters. It is a Linux based tool that can perform attacks in the pre-shared keys for WPA networks. The tool has a command-line interface and is able to perform dictionary attacks on the wireless networks using a wordlist file. The execution is slow due to the usage of SHA 1 with a seed of SSID but you can still give it a try.
6. OmniPeek
OmniPeek is a packet sniffer and a protocol analyzer tool. Developed by Savvis organization, It is available only for the Windows platform. The tool has a lot to offer if you have an understanding of the protocols. The captured packets can be stored in the SQL database which can be further analyzed and decoded if required. The features can be enhanced by using API plugins. Some 40+ API's are readily available for the tool. You may also extend the tool capabilities by visiting the MyPeek community portal if you wish. The tool is commercially available.
You may also like: Amazing Mobile Hacking Tools and Techniques
7. Airjack
As the name suggests the tool is able to hijack the air i.e. wireless. The tool is able to receive and inject raw packets into the wireless network. It can be used by the developers to tweak the packets and inject it to develop the solution or by wireless hackers. A wireless hacker is able to perform a denial of service attacks by flooding the network with dirty injected packets.
8. InSSIDer
SSID mentioned in capital letters in the name itself suggests the features of this tool. It is a wireless scanner tool which supports both Windows and OS X. The tool was available as an open-source software but not any longer. The tool is able to get information from wireless cards and helps you to choose the best channel available with maximum strength. The signal strength is available in graphical format plotted along time. Various versions of the tool are available and you can choose as per your requirement (you would need to hunt it though).
9. WepAttack
WepAttack can be used to crack 802.11 WEP Keys using a dictionary-based approach. The tool can capture the network dump file received from pcap or libpcap etc. The tool is open source and supports the Linux platform. One thing to be noted here is that the attack is active and not passive in nature. The tool will just test the dictionary words to get the working key. The key requirement for this is a working LAN card.
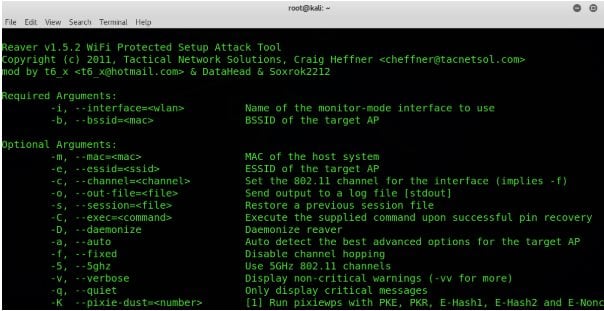
10. Reaver
Reaver uses brute force techniques against WiFi protected setup registrar PINs to get WPA/WPA2 passphrases. One of the best things about this tool is the response time. You can get the passphrase in plaintext within just a couple of hours. If you are using kali, the reaver package is pre-bundled.
11. Fern Wifi Cracker
Fern WiFi Cracker is a python based tool that can be used for WEP/WPA/WPA2 cracking, session hijacking, ARP request replays, and performing brute force attacks. It is able to save the key in the database on a successful attack. It supports an automatic access point attacking feature and has an internal MITM engine as well. This too is also pre-bundled in kali.
12. NetStumbler
In case you are interested to find out about open WiFi networks, this windows tool can help you get this done. You can find rogue access points, network misconfigurations, poor connectivity areas, etc., during wardriving and warwalking kind of activities. The tool is an old veteran and is not updated for a long time so you may face some compatibility issues. This tool interacts actively with the identified networks to gather as much information as possible and hence can be easily detected.
You may also like: Top 20 Trending Computer Forensics Tools of 2018
13. Wireshark
Wireshark is one of the most common network analyzers that are available in the market. It uses the packets captured by WinPcap and libpcap and lets you check the traffic that is flowing through your network. It is available for Linux, Mac, and Windows and is a GUI based tool. The tool captures and presents micro-level details of the packets captured. If you know what you are searching for, you may find this tool very helpful. Since the number of packets captured can be huge, the tool has the option for filtering the packets based on protocol type, strings, etc.
14. Cloudcracker
Cloudcracker is a cloud-based solution for cracking the passwords of various utilities. The tool uses dictionary-based attacks to crack the passwords. The size of the dictionary ranges up to 10 digits. Just upload the handshake file along with a few other details and you are all set.
15. CommView for WiFi
CommView for WiFi is a packet analyzer software. It is GUI based and can monitor wireless 802.11 a/b/g/n networks. Packets are captured and information like strength, access points, network connections can be identified. If you just want to analyze the traffic on your machine, you can prefer a non-wireless CommView edition.
16. Wifiphisher
Wifiphisher is a free WiFi hacking tool that mounts automated phishing attacks against wireless networks to find out the username and password details or infecting the victim with ‘malware’. It comes pre-installed for Kali Linux and can be used seamlessly on Windows, MAC, and LINUX operating systems.
Source: github.com
The only factor that differentiates Wifiphisher from other WiFi hacking tools is that when attempting to breach wireless networks it launches a Social Engineering attack. That is a completely different vector and doesn’t need any brute forcing. Wifiphisher attacks its victims in three crucial phases:
De-authenticating the victims from their access points
Make victims join a rogue access point by sniffing the area and copying the target access points
Serve the victims with a realistic specially-customized phishing page
17. KisMac
KisMac is a wireless network discovery hacking tool specifically for Mac OS X. This classic 802.11 WEP/WPA cracking tool is not for beginners, rather, quite popular among advanced professionals. It tries to crack WEP and WPA keys by scanning for networks passively on supported WiFi cards by any flaw or leveraging any flaw or using brute force.
Source: kismac-ng.org
KisMAC has many features that make it similar to another hacking tool Kismet. This tool can help you collect crucial information about surrounding wireless networks. It has a security scanner app that lets you sketch wifi maps, shows you the logged-in clients, and detect SSIDs.
18. Wifite
Wifite offers useful password cracking features and is compatible with Linux based operating systems. It is capable of attacking several WEP, WPA, and WPS encrypted networks in a row. Wifite is the hot favourite in the industry for Pentesters. It is an ideal choice to test your wifi hacking skills and examine clients’ wireless networks for security susceptibilities.
Source: github.com
The core aim of Wifite is to be the “set it and forget it” WiFi auditing software that is customizable to be automated with only a couple of arguments. The Windows version of this tool isn’t available. You can find it either in the kali Linux operating system or backtrack operating system.
19. WepDecrypt
WepDecrypt is written in the C language and is one of the most effective wireless hacking tools for guessing WEP keys by performing key generator, distributed network attack and dictionary attack. WebDecrypt is a great tool for beginners and requires a few directories to function seamlessly.
Source: wepdecrypt.sourceforge.net
A key feature of WebDecrypt as a hacking software in 2021 is that it has its own key generator, implements packet filters, and functions perfectly in Windows-based OS.
20. Pyrit
Pyrite is a free wireless hacking tool hosted on Google code for executing attacks on IEEE 802.11 WPA/WPA2-PSK authentication. For cracking the WPA/WPA-2 passwords this tool executes brute force attacks. There’s a possibility that this tool might disappear shortly but currently, it works on multiple operating systems such as Linux, MacOS X, FreeBSD.
Source: code.google.com
A couple of Pyrit’s abilities are:
- Analyze the captured files to identify crackable handshakes
- Benchmark a computer's CPU speeds
- Tap into GPU password-cracking power
Two vital powers of Pyrit are true brute force and dictionary attacks depending on the handling capacity of a particular wireless system.
21. Network Mapper (NMAP)
Network Mapper which is referred to as NMAP is an open-source wireless hacking tool for network discovery and vulnerability scanning. This tool is used extensively by network administrators for a range of purposes like:
- Determining what devices are running on their systems
- Detecting security risks
- Identifying available hosts and the services they offer
- Finding open ports
Source: nmap.org
NMAP is one of the best hacking tools because it is quite versatile, usable, and is loaded with a variety of features for making security scanning seamless. Initially, NMAP was only compatible with Linux but gradually it started functioning on other operating systems such as Windows, IRIX, Solaris, AmigaOS, BSD variants (including OS X), HP-UX, etc.
22. IKECrack
IKECrack is an open-source wireless hacking tool for cracking IPsec/IKE authentication. This tool is specially built to capture Internet Key Exchange packets. Also, it's an effective tool for VPN network cracking. IKECrack hacks into a wireless network by obtaining and using the identity and secret key combinations of the network.
Source: ikecrack.sourceforge.net
IKECrack is capable of performing potent brute force attacks and implementing cryptography tests which is why this tool is an ideal choice for clients who have the possibility of such tests.
23. KARMA
KARMA is an open-source hacking software that uses the probing techniques leveraged by a client of a WLAN. The station explores the list of preferred wifi networks and searches for a Wireless LAN for making the SSID open to access for the attackers.
Source: karma-runner.github.io
KARMA leverages the disclosed SSID for impersonation of a valid WLAN and grabs the attention of the listening attacker to the station. Once a victim falls into the trap of KARMA, the tool steals crucial credentials like logins and passwords by redirecting FTP, web, and email requests to phone sites.
24. Yersinia
Yersinia is an open-source wireless hacking software designed for Unix-like operating systems. This tool is capable of detecting susceptibilities in Layer 2 network protocols. It is a powerful tool for analyzing and testing the deployed wifi networks. Yersinia is capable to identify security vulnerabilities in the following network protocols:
- Spanning Tree Protocol (STP)
- Hot Standby Router Protocol (HSRP)
- Cisco Discovery Protocol (CDP)
- Inter-Switch Link Protocol (ISL)
- Dynamic Trunking Protocol (DTP)
- Dynamic Host Configuration Protocol (DHCP)
- VLAN Trunking Protocol (VTP)
Source: sectools.org
Yersinia is capable of executing multiple attacks over diverse protocols and is an effective penetration testing tool. It’s a widely accepted and valuable wireless hacking software.
25. Airgeddon
Airgeddon is one of the latest and advanced wireless hacking tools. Similar to other hacking solutions it is capable of switching your interface mode from “Monitor” to “Managed”. Its core purpose is to audit wireless networks by using multi-use bash scripts for Linux systems.
Source: github.com
One of the key features of Airgeddon is that it can perform brute force attacks after decrypting the offline passwords that have been captured. Also, it allows penetration testers to perform a DoS attack over a wifi network by leveraging another popular Wireless tool called aireplay-ng and various methods such as mdk3, mdk4.
Conclusion
There are many wireless hacking tools available in the market, 15 of which we have discussed in this article. It is to be noted that the tools are discussed in random order and not in any form of priority or superiority over the other. The tools discussed here are not only designed for wireless hackers but are also used by WiFi admins and programmers working on WiFi-based projects alike. These tools can either be used for monitoring the network or cracking the keys to getting access. You may need to use multiple tools to get the desired output as none of the tools would fulfil all the requirements. As a wireless hacker or security professional, you should have some of these tools in your arsenal readily available for quick analysis. Some of the tools perform brute force to crack the keys, make sure th